Crypto Basics
Base64 Encoding
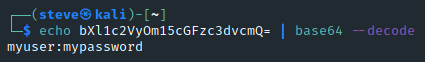
The challenge gives you an encoded string. An easy way to decode base64 is using the command line. Use this command:
echo <encoded string> | base64--decode
Other Encoding
This challenge gives you an xor encoded string. For this, the easiest method is to use an online tool. I found this tool helpful: https://strelitzia.net/wasXORdecoder/wasXORdecoder.html

Plain Hashing
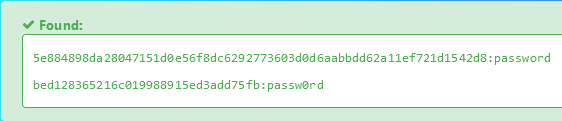
This challenge wants you to decode a MD5 hash. The best way is using an online decoder, such as: https://hashes.com/en/decrypt/hash
Private Key
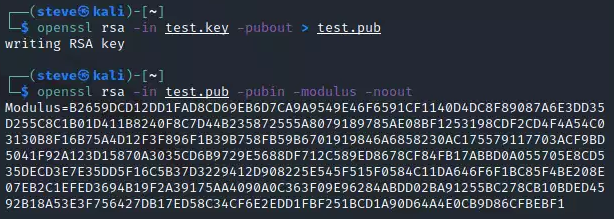
This challenge is finding the modulus and the signature based on the modulus of a private RSA key. First to find the modulus you can save the private key as test.key, then run this command openssl rsa -in test.key -pubout > test.pub, followed by this command openssl rsa -in test.pub -pubin -modulus -noout
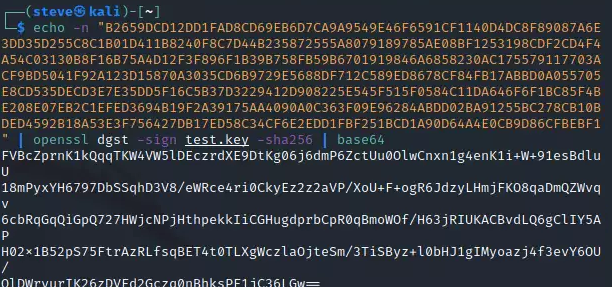
For the signature, enter this command: echo -n "<modulus>" | openssl dgst -sign test.key -sha256 | base64
Java cacerts
For this challenge we need to fire up a Docker container, because I am running WebGoat in Docker, I already have Docker up and running! docker run -d webgoat/assignments:findthesecret. The user in the container does not have permission to see the root directory, to get past this we can use docker cp to copy the /etc/passwd file from the container to our host, edit the file, then cp it back to the container.
docker cp <docker container id>:/etc/passwd pass.txt
vim pass.txt
Change the UID & GID of the user webgoat from 1000:1000 to 0:0, the file should look like this
~# cat pass.txt
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
_apt:x:100:65534::/nonexistent:/bin/false
webgoat:x:0:0::/home/webgoat:
Now copy the file back docker cp pass.txt 098f135c6b08:/etc/passwd
Access the container docker exec -it <docker container id> /bin/bash
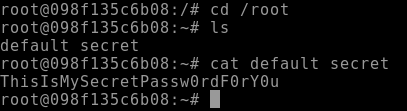
Run the decryption against the secret file
echo "U2FsdGVkX199jgh5oANElFdtCxIEvdEvciLi+v+5loE+VCuy6Ii0b+5byb5DXp32RPmT02Ek1pf55ctQN+DHbwCPiVRfFQamDmbHBUpD7as=" | openssl enc -aes-256-cbc -d -a -kfile default_secret
